Harmonize Security for Users, Devices & Access
Empowering Secure Digital Transformation: Unify Protection for Seamless Operations
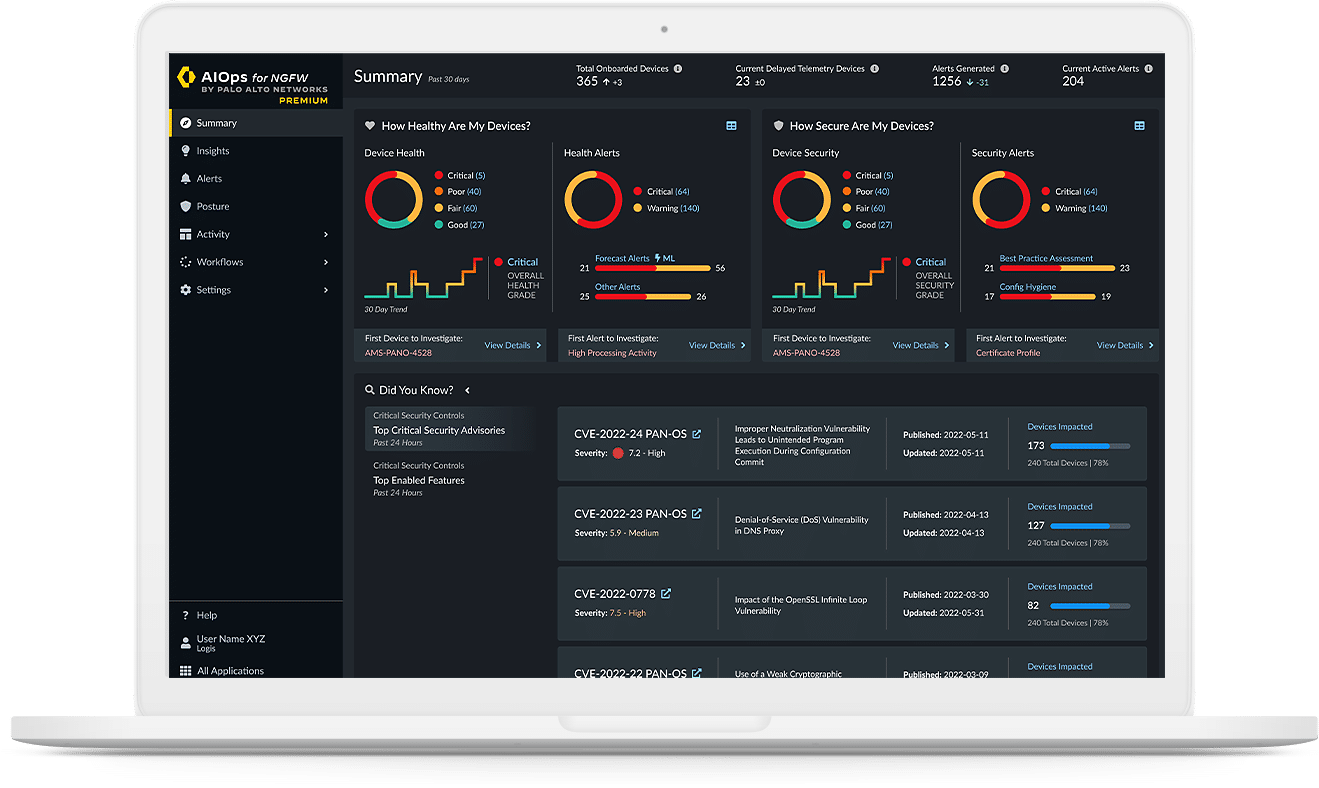
In today’s interconnected world, it is crucial to establish a comprehensive security framework that safeguards sensitive data, mitigates risks, and enables efficient collaboration. Our cutting-edge solutions empower businesses to achieve this harmony, protecting against evolving threats while maintaining user productivity.