Vulnerability Assessment Services
Strengthen Your Defenses and Protect Your Digital Assets
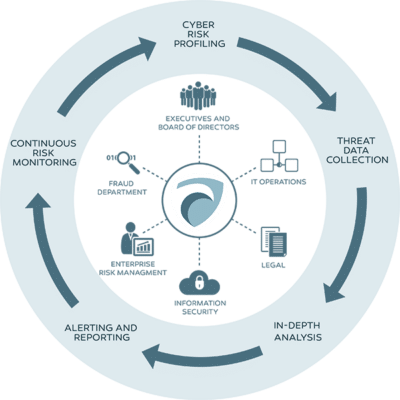
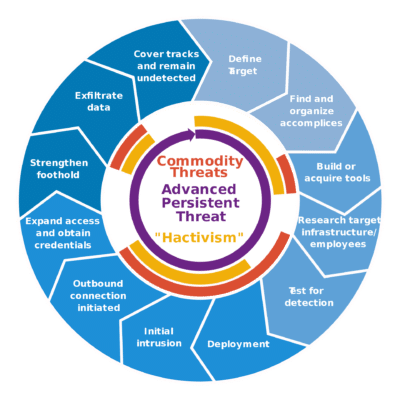
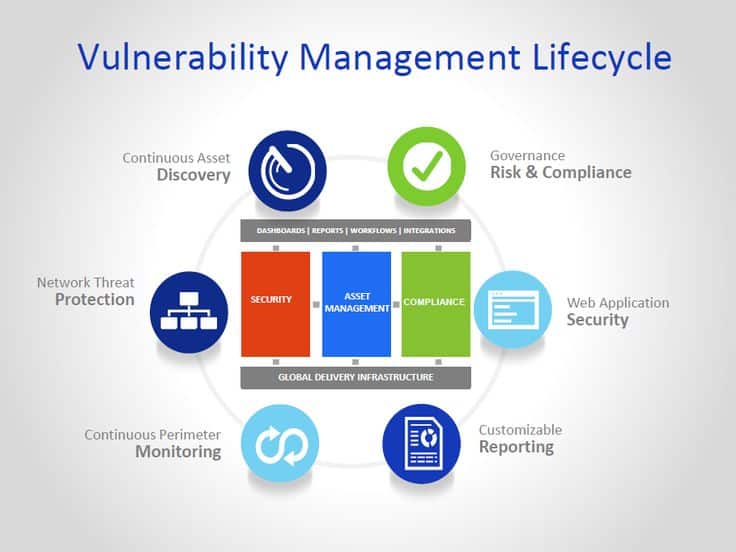
Discover our comprehensive vulnerability assessment services to proactively identify weaknesses in your systems, applications, and infrastructure. Strengthen your defenses, mitigate risks, and safeguard your valuable digital assets with our expert analysis and actionable recommendations.
In today’s ever-evolving threat landscape, understanding and addressing vulnerabilities is crucial to maintaining a robust security posture. At FCS, we offer comprehensive vulnerability assessment services designed to proactively identify weaknesses in your systems, applications, and infrastructure. Our expert analysis and actionable recommendations enable you to strengthen your defenses, mitigate risks, and protect your valuable digital assets.