The US DOJ described the North Korean hackers as “the world’s leading bank robbers” and “a criminal syndicate with a flag.”
The US Department of Justice has unsealed today new charges against the Lazarus Group, a codename given to North Korea’s state-sponsored military hacking groups.
The new indictment expands charges initially brought against Park Jin Hyok, a North Korean military hacker the US charged in September 2018 for his involvement in the Sony hacks, WannaCry ransomware attacks, and bank cyber-heists.
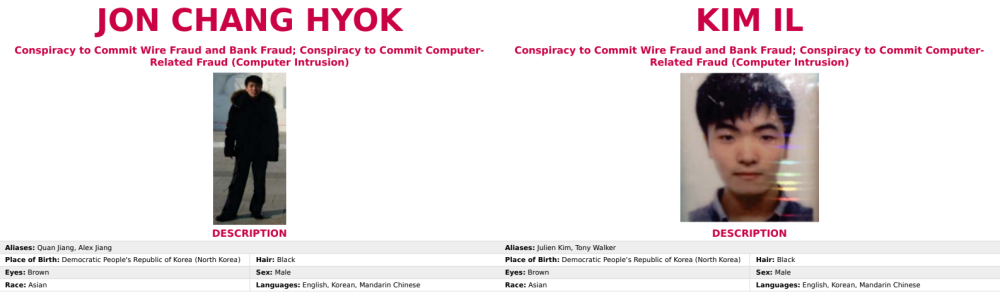
The new indictment unsealed today charges two additional North Korean hackers, namely Jon Chang Hyok (전창혁), 31, and Kim Il (김일), 27, and expands the charges brought against Park in 2018.
US officials say the three hackers are part of units of the Reconnaissance General Bureau (RGB), a North Korean military intelligence agency, part of which they participated in a worldwide hacking campaign that dates back to 2014 and includes the likes of:
- The hack of Sony Pictures Entertainment in 2014, in retaliation for the studio releasing The Interview movie.
- Cyber-heists at banks in Vietnam, Bangladesh, Taiwan, Mexico, Malta, and across Africa. The group targeted the bank’s SWIFT money transfer system in attempts to steal more than $1.2 billion in funds.
- ATM cash-out attacks using the FASTCash malware. One successful such attack took place in October 2018 when the group stole $6.1 million from Pakistan’s BankIslami.
- The WannaCry ransomware outbreak of May 2017.
- Creating and spreading malware-laced cryptocurrency apps that stole users’ funds. Examples include Celas Trade Pro, WorldBit-Bot, iCryptoFx, Union Crypto Trader, Kupay Wallet, CoinGo Trade, Dorusio, CryptoNeuro Trader, and Ants2Whale.
- Hacks of cryptocurrency exchange portals. The DOJ said the RGB targeted hundreds of such entities and stole tens of millions of US dollars.
- Spear-phishing campaigns targeting US defense contractors, energy companies, aerospace companies, technology companies, the United States Department of State, and the United States Department of Defense.
- Creating a fake cryptocurrency company and releasing the Marine Chain Token. The US DOJ said the scheme would have allowed users to purchase ownership of marine vessels via a cryptocurrency token, allowing the North Korean state to gain access to investor funds and bypass US sanctions.
US officials said that while campaigns were geared towards intelligence collection, most were criminal endeavors to gather funds for the hermit kingdom’s regime.
Assistant Attorney General John Demers described the three hackers and the Lazarus Group as “the world’s leading bank robbers” and “a criminal syndicate with a flag.”
ONE MORE MONEY MULES CHARGED
But today, the DOJ also said it charged a Canadian national named Ghaleb Alaumary for helping the Lazarus Group launder some of their stolen funds.
“Alaumary was a prolific money launderer for hackers engaged in ATM cash-out schemes, cyber-enabled bank heists, business email compromise (BEC) schemes, and other online fraud schemes,” DOJ officials said.
He allegedly organized crews of money launderers in the US and Canada to receive stolen funds and then relay the funds to other accounts under the hackers’ control.
This included laundering funds stolen from the BankIslami ATM cash-out attack, another ATM cash-out from an Indian bank that took place in 2018, and funds stolen from a Maltese bank in 2019.
Alaumary is now the third Nortk Korean money muled charged in the US after the DOJ charged two Chinese nationals in March 2020.
A copy of today’s indictment is available here, in PDF format.
Besides the DOJ charges, the US Cybersecurity and Infrastructure Security Agency has also released a report today on the AppleJeus malware, which the Lazarus Group has often used during attacks on cryptocurrency exchange portals.


