When individuals and organizations alike rely so much on their computers to get work done, there is nothing they hate more than being held hostage by ransomware and often hold a deep resistance to paying the demanded ransom. After all, when there is no guarantee the criminal will keep his word and release the files, why pay up? To avoid paying then, victims can hire an IT consultancy to help them unlock their files.
However, Check Point Research recently discovered a new development in the ransomware industry of an IT consultancy, in this case a Russian company named ‘Dr. Shifro’, that claims to legitimately unlock encrypted files but in fact merely pays the ransomware’s creator themselves and passes on the cost to the victim – at a massive profit margin.
Ransomware By the Numbers
In 2017, ransomware took center stage with the catastrophic attacks of WannaCry, NotPetya and Bad Rabbit, and it has continued to be a major menace this year too. From the crippling effect it had on the City of Atlanta earlier this year, preventing vital services within the city from functioning, to the constant havoc caused on the healthcare sector. Indeed, the healthcare industry is one which continues to bear the brunt of ransomware attacks with some ransom demands reaching as high as $2.8 million in some cases. Such demands are considered rare, however, with the average demand around $10,000.
According to Europol’s 2018 Internet Organized Crime Threat Assessment, the ransomware industry is now worth an estimated $5 billion that is drained yearly from the global economy. In fact, it is very much a staple attack tool for cyber criminals everywhere and has also allowed for subsidiary cottage industries to spring up around it. These include ransomware-as-a-service (RaaS) offerings that allow those with very low technical know-how to get in on the act by spreading the ransomware built by those more proficient. In addition, ransomware affiliate programs have grown to allow the ransomware creators to claim a cut from their affiliates who spread this malware.
As we will now see, though, the discovery of Dr. Shifro is the latest development of the ever growing and changing ransomware landscape.
Who You Gonna Call?
When access to much needed files are locked and held to ransom at such high prices, it’s no wonder that organizations will do almost anything to restore their access to them.
At this point there are three possible options available:
- Restore any locked files from backup.
- Pay the ransom to the threat actor responsible for locking those files in the first place.
- Pay an IT consultant who may be able to unlock the files without paying the ransom.
For those with no file back-up plan in place or who do not want to pay the ransom amount, the third option is usually a sensible choice. Unfortunately, though, it is here that Check Point Research discovered a unique and worrying new development in the ransomware landscape.
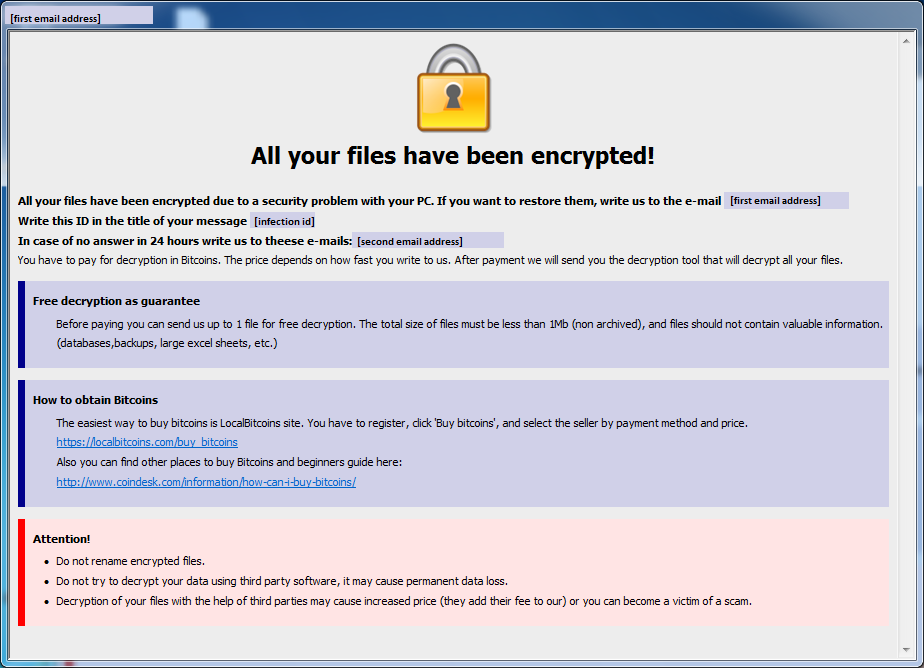
Something first seemed off when our team came across a certain ‘IT consultancy’, promoted online as ‘Dr. Shifro’, that offered only one service – helping ransomware victims unlock their files. For an IT consultancy to offer only one unique service is highly unusual and arguably suspicious.
In addition, Dr. Shifro promises to perform dazzling feats of cyber wizardry to unlock files held captive by the Dharma/Crisis ransomware (for which no decryption key is available), among others. So, whereas IT services such as these usually explain they can only try and do their best, with no promises made, it seemed strange that Dr. Shifro guarantees to unlock files for ransomware that has no public key even available. Now that’s quite a promise!
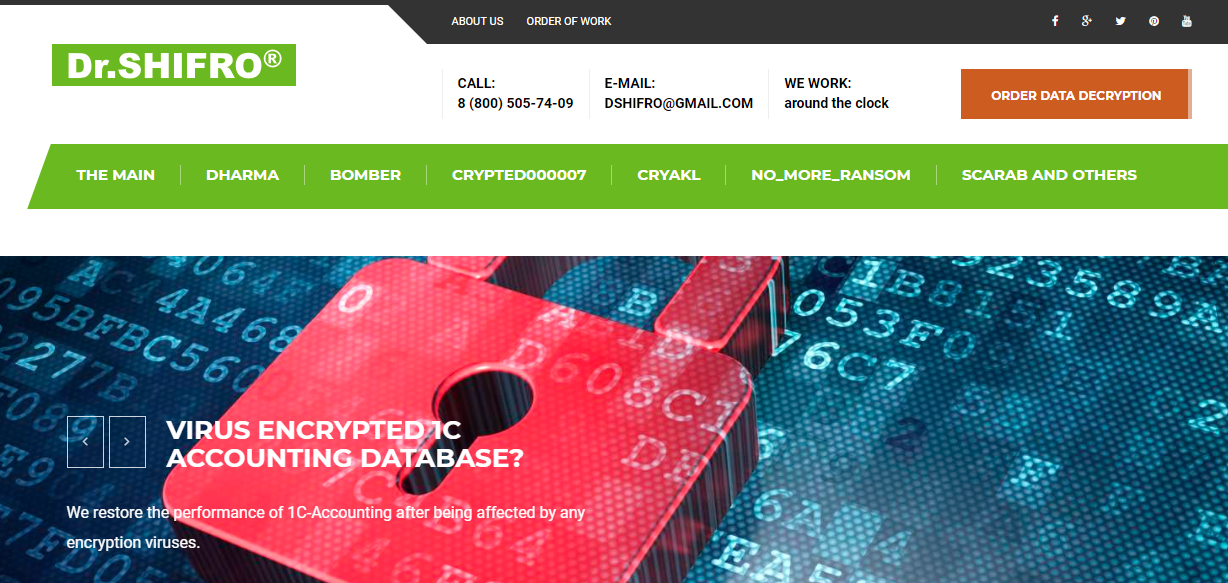
Dr.Shifro’s website advertising his ransomware decryption services.
After some undercover investigation, it soon appeared that Dr. Shifro was actually making contact with the ransomware’s creator themselves and making a deal with them to unlock the victim’s files in return for the ransom payment ($1300). Dr. Shifro would then pass that cost on to the victim with his own fee charged on top (another $1000).
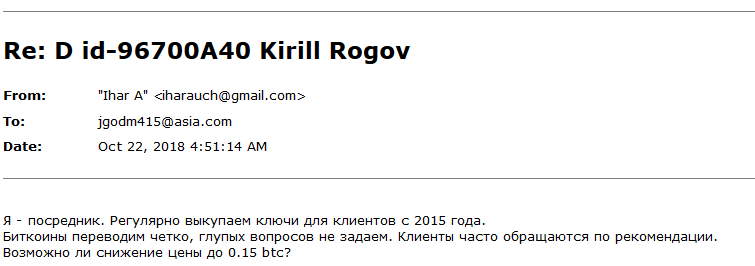
Below is part of the correspondence between Dr. Shifro and a ransomware creator where we can get a glimpse of how Dr. Shifro’s ‘consultancy’ works. By connecting directly with the threat actor to collect the decryption key, in return for payment, Dr. Shifro simply acts as a broker between victim and attacker.
Part of the correspondence between Dr. Shifro and the Ransomware creator.
Translation of Dr.Shifro’s email to ransomware creator: I’m an intermediary. We redeem keys for clients since 2015 on a regular basis. Send bitcoins tight, don’t ask dumb questions. Clients frequently addressed under recommendation. Could you give a discount to 0.15 btc?
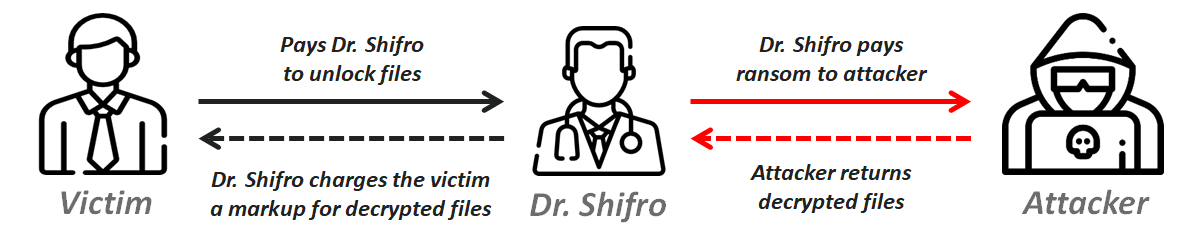
This creates an attractive business model. After all, it would seem that all parties win. The victim has their files decrypted, the cyber criminal gets his ransom payment and Dr. Shifro, at an almost 100% markup, earns a handsome ‘broker’ fee.
Dr.Shifro’s business model
Key Takeaways
The first thing to bear in mind when coming across services like Dr. Shifro is “if it sounds too good to be true, it probably is.” Whereas there are legitimate IT consultancies that can help you recover your systems and files from a ransomware attack, they will usually not make promises they cannot keep. In fact, they will only be as confident in what they can offer as the decryption keys that are already publicly available online and merely perform these decryption services for those who may be unable to do so themselves. Anyone claiming otherwise should be approached with caution.
With ransomware being such a devastating and profitable form of attack, we are certain to see the evolution of both the malware itself and the ecosystem it operates within continue. As well as the Ransomware-as-a-Service and ransomware affiliate industry that has sprung up in recent years, the creativity of cyber criminals clearly seems to still have much steam. Indeed, the business model that Dr. Shifro has created is an attractive one that could easily be replicated by other entrepreneurial scam artists and thus serves as a new development of the ransomware industry that both individuals and organizations should be wary of.
Of course, organizations are well advised to be using anti-ransomware prevention solutions across their network in order to avoid being infected in the first place. For this reason we recommend solutions that do not rely on signatures only to identify the various ransomware strains and is able to emulate and extract suspicious files in a virtual sandbox and automatically recover encrypted files.
If you have been affected by ransomware, please visit Europol’s ‘NoMoreRansom’ site for further advice and ways to unlock encrypted files.
For full technical details on how this undercover investigation was carried out, please visit Check Point Research.
For more information about how you can protect your organization from ransomware, please read about Check Point’s Anti-Ransomware solution.