Introduction
During the closing weeks of 2020 a Cyber Security attack became one of the main headline news stories of what had already been a news-rich year. Attributed to a campaign that began months earlier, the information security teams of government agencies and private organizations quickly shifted their focus to a vulnerability in the SolarWinds Orion solution, which could open a backdoor into organizational communications networks. Dubbed Sunburst, this incident called into question the trustworthiness of the primary technology tools that organizations use to manage their corporate technology resources.
As with any security incident, security practitioners would initially focus on identifying signs of potential Sunburst activities in their networks and systems. From there they would prioritize immediate remediation activities. Once these initial efforts were complete, security teams would need to consider broader structural changes to their security programs.
This blog provides information intended to assist with these primary phases and is structured according to the following flow:
- A summary of the Sunburst breach
- Network mitigations
- Host remediation
- Additional considerations
- Potential considerations for longer-term security improvements, including guidance on DevOps, Endpoint and cloud environments, according to the Zero-Trust Architecture framework
Some of the recommendations included in this blog apply to what was known about the Sunburst event at the time of writing. FCS will update the document as more information becomes available.
About the Sunburst event
On the 8th of December 2020, FireEye, a US-based Cyber Security company, notified the market that it was attacked by what the company believed was a nation-state actor who gained access to some of FireEye’s Red Team tools.
Five days later, on the 13th of December 2020, reporting in major US news outlets indicated that US government agencies had been breached in what appeared to be a complex Cyber Attack, and on that same day the US Cyber & Infrastructure Security Agency (CISA) issued an emergency directive to all US Federal civilian agencies to “review their networks for indicators of compromise and disconnect or power down SolarWinds Orion products immediately.”
The CISA notification was followed by a SolarWinds filing with the Securities and Exchange Commission (SEC). That filing noted that SolarWinds was made aware of a “cyberattack that inserted a vulnerability within its Orion monitoring products which, if present and activated, could potentially allow an attacker to compromise the server on which the Orion products run.”
SolarWinds Orion
SolarWinds Orion is an enterprise software suite that includes performance and application monitoring and network configuration management. SolarWinds Orion is used to monitor and manage on-premise and hosted infrastructures. To provide SolarWinds Orion with the necessary visibility into this diverse set of technologies, it is common for network administrators to configure SolarWinds Orion with pervasive privileges, making it a valuable target for adversary activity.
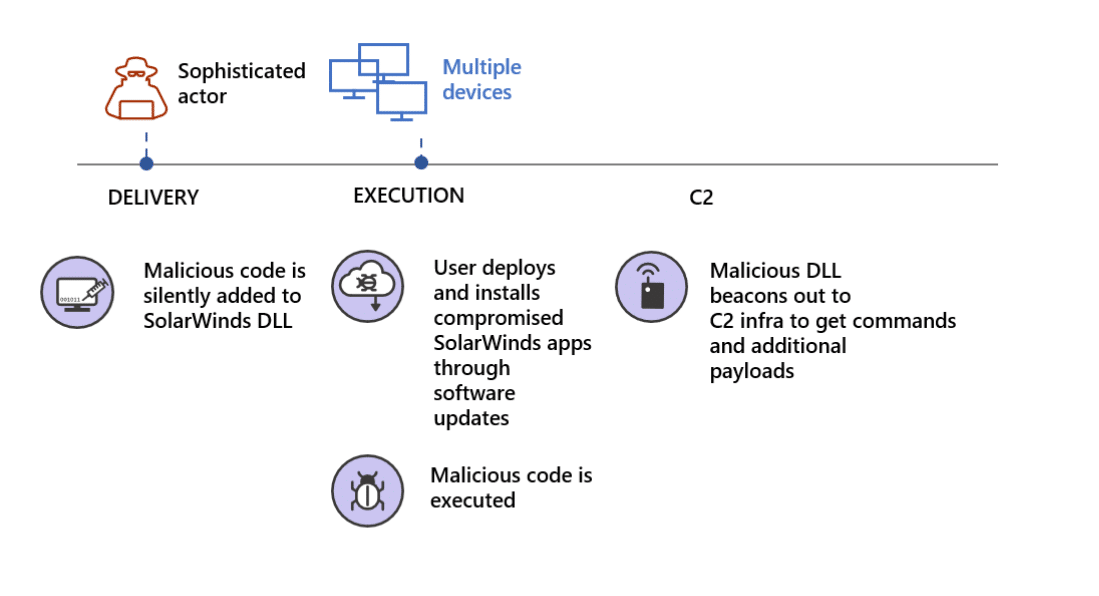
According to the Cybersecurity and Infrastructure Security Agency (CISA), the SolarWinds Orion export, Sunburst, was a supply chain attack that compromised and impacted several U.S. government agencies, critical infrastructure entities. The incident also affected private sector organizations using an advanced persistent threat (APT) attack that started in March 2020.
According to the CISA’s analysis, the threat actor added a malicious version of the binary solarwinds.orion.core.businesslayer.dll into the SolarWinds software lifecycle, which was then signed by a legitimate SolarWinds code signing certificate.
The compromised binary, once installed, calls out to a victim-specific avsvmcloud.com domain using a protocol designed to mimic legitimate SolarWinds protocol traffic. After the initial check-in, the hacker can use the Domain Name System (DNS) response to selectively send back new domains or IP addresses for interactive command and control traffic (C&C).
SolarWinds Orion typically uses a significant number of highly privileged accounts to perform normal business functions. Successful compromise of one of these systems can therefore enable further action. Consequently, entities that observe traffic from their SolarWinds Orion devices to avsvmcloud.com should not immediately conclude that the hacker leveraged the SolarWinds Orion backdoor. Instead, additional investigation is needed into whether the SolarWinds Orion device engaged in further unexplained communications.
According to the CISA advisory, the following SolarWinds Orion products were impacted:
- Orion Platform 2019.4 HF5, version 2019.4.5200.9083
- Orion Platform 2020.2 RC1, version 2020.2.100.12219
- Orion Platform 2020.2 RC2, version 2020.2.5200.12394
- Orion Platform 2020.2, 2020.2 HF1, version 2020.2.5300.12432
Broader significance of the incident
Among the next steps that the attacker took after establishing the initial foothold was to compromise the Security Assertion Markup Language (SAML) signing certificate using escalated Active Directory privileges. Once this was accomplished, the hacker created unauthorized but valid tokens (token id) and presented them to services that trust SAML tokens from the environment. These tokens can then be used to access resources in hosted environments, such as email, for data investigation and exfiltration via authorized application programming interfaces (APIs).
SAML is used by many business applications, including:
- SaaS Applications that requires SAML for single-sign-on (Business Applications, Email Services e.g.)
- File storage services (such as SharePoint, OneDrive for Business)
- Kubernetes and Containers environments that requires Active directory
These types of solutions are important for espionage and data collection efforts. Access to email and file repositories provides visibility into troves of interesting communications and content MITRE ATT&CK® Techniques used in Sunburst attack
The MITRE ATT&K® framework helps provide context to the Sunburst campaign. The following represent known tactics and techniques:
- Query Registry [T1012]
- Obfuscated Files or Information [1027]
- Obfuscated Files or Information: Steganography [T1027.003]
- Process Discovery [T1057]
- Indicator Removal on Host: File Deletion [T1070.004]
- Application Layer Protocol: Web Protocols [T1071.001]
- Application Layer Protocol: DNS [T1071.004]
- File and Directory Discovery [T1083]
- Ingress Tool Transfer [T1105]
- Data Encoding: Standard Encoding [T1132.001]
- Supply Chain Compromise: Compromise Software Dependencies and Development Tools [ [T1195.001]
- Supply Chain Compromise: Compromise Software Supply Chain [T1195.002]
- Software Discovery [T1518]
- Software Discovery: Security Software Discovery [T1518.001]
- Create or Modify System Process: Windows Service [T1543.003]
- Subvert Trust Controls: Code Signing [T1553.002]
- Dynamic Resolution: Domain Generation Algorithms [T1568.002]
- System Services: Service Execution [T1569.002]
- Compromise Infrastructure [T1584]
Security practitioners interested in reviewing comprehensive lists of indicators of compromise can find them in multiple online publications. The CISA alert referenced below is one such example.
This event continues to evolve and researchers are providing updated information on a regular basis. The following sources provide relevant background:

